Situation
The nature of cloud landscapes is that they are highly dynamic and grow steadily. Keeping grip on the current level of security can be a challenge. AWS provides a great tool to get a consolidated overview, particularly in AWS Landing Zone architectures: AWS Security Hub
AWS Security Hub
In the following post we will introduce AWS Security Hub and two security standards we recommend you consider for your AWS accounts.
The security standards are shipped with AWS Security Hub and can be enabled with a simple click.
Note: Please be aware that both security standards deploy managed AWS Config rules that will generate costs.
The following diagram shows the concept behind AWS Security Hub:
https://acai.gmbh//images/blog/aws-securityhub-standards/decision_tree.svg does not existAWS Security Hub is made for multi-account setups. You can specify a master account (usually the Core Auditing Account) and invite member accounts to the master.
Recommended Standards
We recommend enabling the following standards. Per enabled security standard you will get an aggregated security score across all security controls, enabled for the security standard.
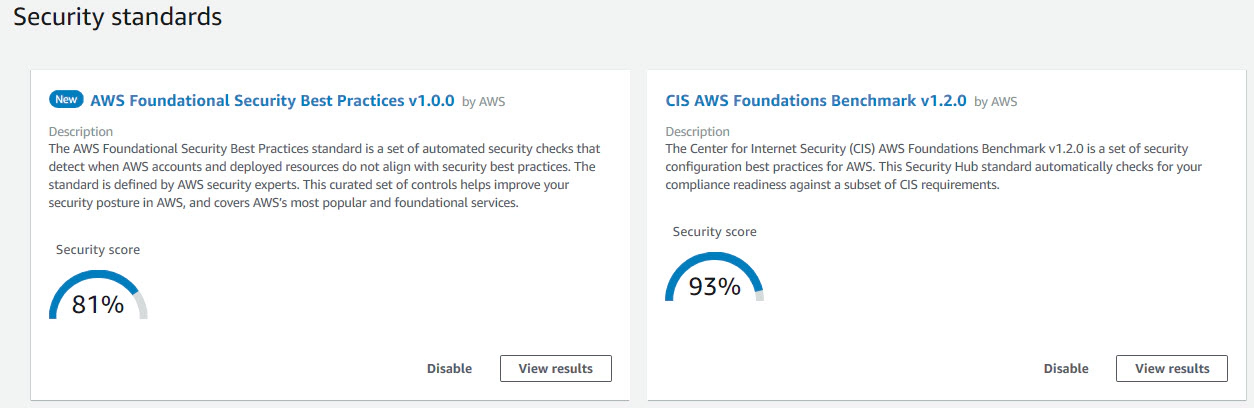
CIS AWS Foundations Benchmark
The Center for Internet Security (1) provides a great set of benchmarks for different technologies. For AWS they provide the CIS Amazon Web Services Foundations Benchmark and the CIS Benchmark for Amazon Web Services Three-tier Web Architecture.
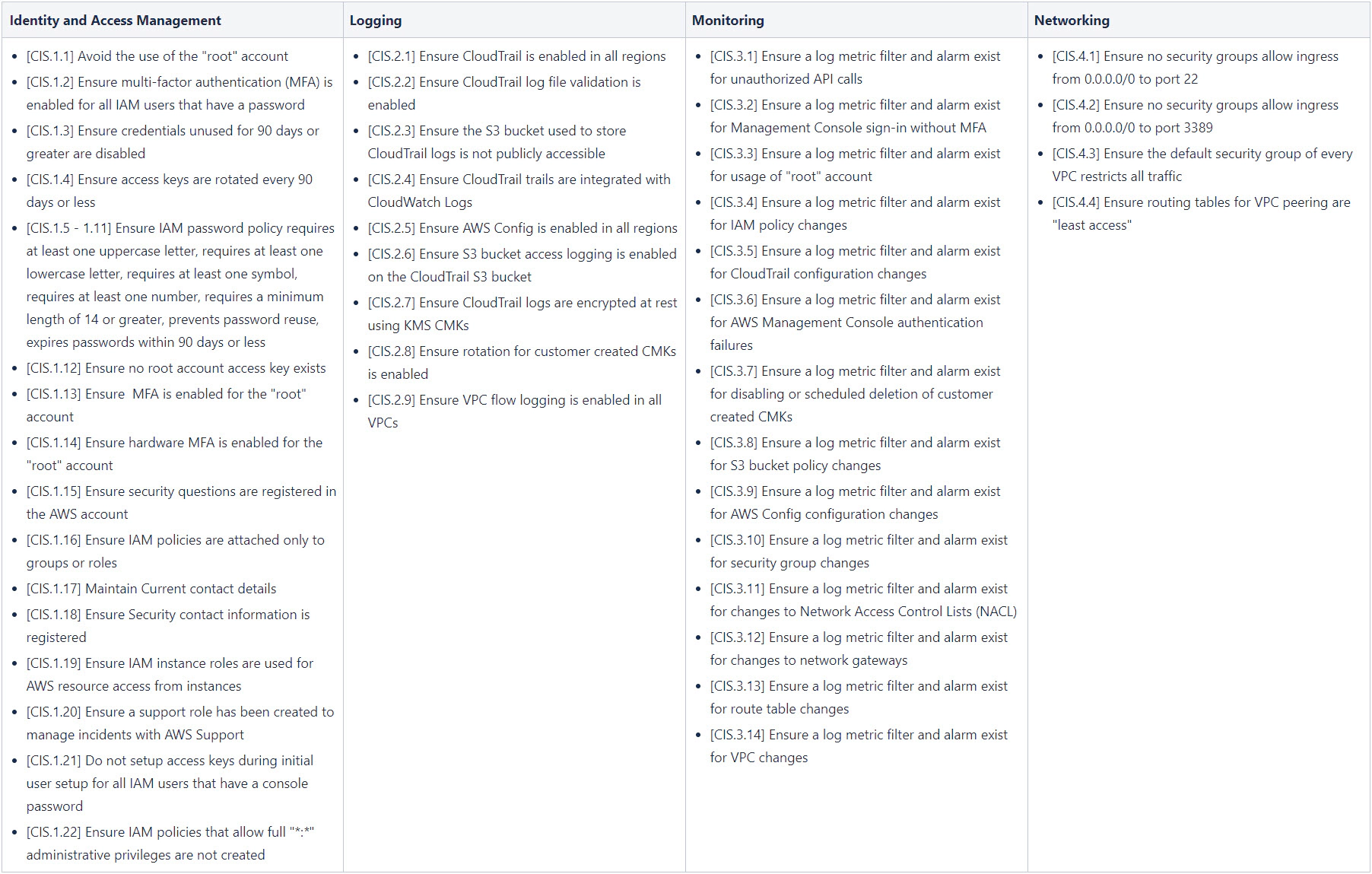
As mentioned AWS Security Hub comes with the CIS AWS Foundations Benchmark [2][3] which consists of 49 security controls from the four following domains:
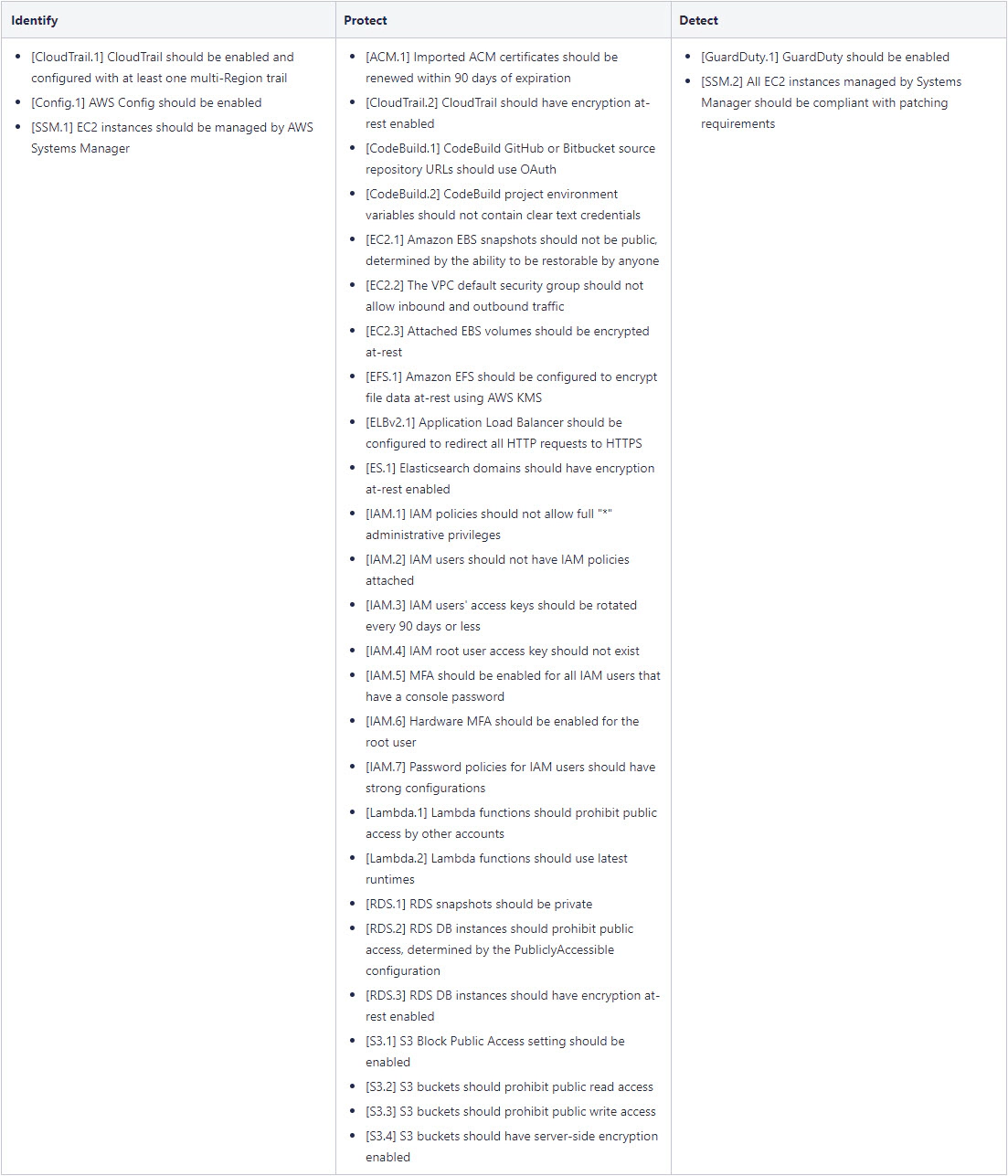
AWS Foundational Security Best Practices
Since Q2-2020 the AWS Foundational Security Best Practices [4] security standard has been available at AWS Security Hub. It consists of 31 security controls that belong to one of the following categories, which are based on the functions described in the NIST Cybersecurity Framework.
We are ACAI Consulting – specialized in AWS Multi Account Security and Governance. If you have any questions, feel free to get in touch with us: blog@acai.gmbh
References
[1] https://www.cisecurity.org/
[2] AWS_CIS_Foundations_Benchmark.pdf